Cloud and Kubernetes Detection and Response
Built on eBPF, Spyderbat instantly and continuously visualizes all runtime app behavior—
from the kernel to Kubernetes and the cloud—to reduce alerts by 2-3 orders of magnitude, and automatically block attacks in real time.


Trusted in Production




Stop the Attacks that CSPMs Miss
- Cut investigation time from hours to minutes:
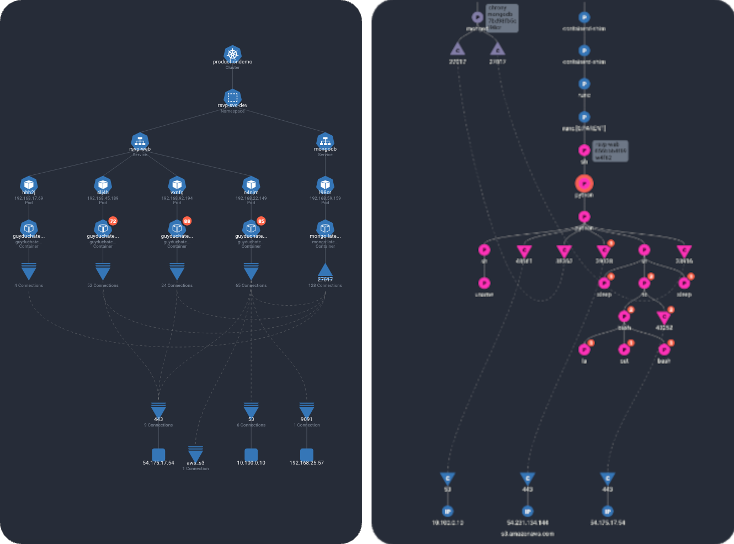
See clear chained events that pinpoint exactly what went wrong, when it happened, what led to it, and the potential for downstream impact. - Reduce alert volume by 3x:
Never-before captured runtime context lets Spyderbat suppress truly useless noise to surface real risk in real time, without overwhelming alerts. - Stop attacks in their tracks:
Automatic attack detection and remediation works in parallel with learned guardrails that protect known-good processes, to stop threats and protect uptime. - Low agent overhead:
Less than 2% usage due to eBPF and SaaS architecture - Full visibility and context:
For cloud, across any Linux nodes and entire K8 cluster of containers and pods

Recent Recognition and Shouts
A sampling of freshly minted industry awards, customer testimonials,
and general Spyderbat celebration
Security Time Travel
"...Their platform has distinct components that allow you to see things as they were, as they are, and how they should be."
Read the Article

From the Experts
"Spyderbat is an amazing option for companies looking for rich Kubernetes specific runtime protection."
- James Berthoty, DevSecOps

Startup of the Year
Spyderbat Named “Cloud Security Startup Of The Year” based on innovation and success in information security.
Read the announcement

Isn't it time to actually stop real threats?
Cloud Detection, Investigation and Response
Passive scanners, CSPM, and shift-left guardrails haven't reduced successful breaches. That's why Spyderbat has revolutionized cloud security to automatically find and stop running attacks in real time.
 Limit Interruptions
Limit Interruptions
Buy time to patch on your own schedule with active protection against attacks targeting known vulnerabilities.
 Instant Protection
Instant Protection
Spyderbat detects application drift from built-in Linux services, Kubernetes services, and common commercial applications providing the most resilient defense against outages, as well as unknown and zero-day attacks.
 Clear Value
Clear Value
Detections are mapped to the MITRE ATT&CK Matrix, and visually shown as chained TTPs for both existing and never-before-seen threats.





