In today’s rapidly evolving cloud landscape, organizations are tasked with ensuring robust security while maintaining agility and scalability. Two foundational approaches to cloud security, Shift-Left Security and Shift-Right Security, offer complementary methodologies that, when combined, create a comprehensive cloud security strategy.
Just like we have blue teams and red teams in cyber security, you want two layers of protection with unique perspectives to assure greater and more comprehensive coverage. A single source perspective (CSPM) of a threat will yield a specific set of configuration recommendations and an equivalent set of attack detections against those same misconfigurations. If you were to follow CSPM’s recommendations perfectly, you may be missing something CDR capabilities will pick up. From a security and “defense-in-depth” perspective, you are much better off having the two work as checks and balances of each other. Otherwise, you’ve got the proverbial fox watching the hen house.
By integrating the proactive measures of Shift-Left Security with the reactive capabilities of Shift-Right Security, organizations can ensure end-to-end security throughout the cloud lifecycle. This approach not only strengthens security at every stage but also establishes essential checks and balances, enabling a seamless and resilient security strategy.
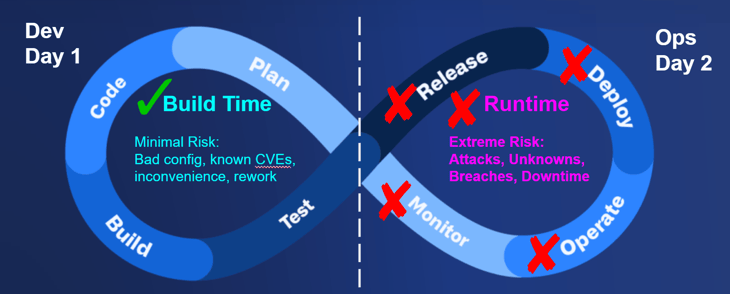
Shift-Left Security: Strengthening the Foundation
Shift-Left Security emphasizes proactively embedding security into the development and deployment phases. This approach ensures that risks are identified and mitigated early, reducing vulnerabilities before they reach production.
Key Solutions in Shift-Left Security
Cloud Security Posture Management (CSPM)
CSPM solutions are designed to continuously assess and improve the security posture of cloud environments. They help organizations identify and remediate risks, ensure compliance, and maintain visibility across multi-cloud environments. Key features include:
-
Continuous Monitoring: Regularly scans cloud environments for misconfigurations and vulnerabilities.
-
Compliance Management: Ensures adherence to regulatory frameworks such as CIS, GDPR, SOC2, PCI DSS, and HIPAA.
-
Risk Assessment: Identifies and prioritizes security risks based on their potential impact.
-
Automated Remediation: Provides automated solutions to fix identified issues.
-
Integration with DevOps: Streamlines security into the DevOps pipeline for continuous compliance and security.
Examples of CSPM vendors: Wiz, Lacework, Orca.
Data Security Posture Management (DSPM)
DSPM focuses on understanding and protecting sensitive data in the cloud by addressing the following questions:
-
Where is your data stored?
-
What type of data are you storing?
-
Who has access to that data?
-
How could someone get to that data?
Notable DSPM vendors include Normalyze, Cyera, and Sentra.
SaaS Security Posture Management (SSPM)
SSPM applies CSPM principles to SaaS applications like Salesforce, Workday, and others. It ensures these platforms are securely configured and compliant with industry standards. Vendors include Netskope, Palo Alto Networks (Prisma), and Zscaler.
Application Security Posture Management (ASPM)
ASPM takes a holistic approach to managing and improving the security of applications throughout their lifecycle. It integrates security into every phase of application development and deployment.
Key players in ASPM: Snyk, Synopsys, Cycode, Legit.
Cloud Native Application Protection Platform (CNAPP)
CNAPP combines CSPM with a broad set of other cloud security tools addressing entitlement management, network security, and runtime posture validation. It attempts to provide a unified approach to securing cloud-native applications.
Shift-Right Security: Real-Time Protection
Shift-Right Security focuses on detecting and responding to threats in real-time, ensuring that active environments remain secure against evolving risks.
Core Component of Shift-Right Security
Cloud Detection and Response (CDR)
CDR solutions enhance visibility, detection, and response capabilities in cloud environments. They address the dynamic nature of cloud workloads and provide:
-
Threat Monitoring: Continuously monitors for suspicious activities, user behaviors, and application anomalies.
-
Incident Response: Quickly identifies, mitigates, and resolves detected threats, often including forensic analysis.
-
Threat Hunting: Proactively searches for hidden threats within the environment.
Key Challenges Addressed by CDR
-
Enhanced Visibility: Provides real-time monitoring of cloud environments to detect threats as they occur.
-
Dynamic Workloads: Adapts to the ephemeral nature of cloud workloads, such as those in Kubernetes environments.
-
Comprehensive Incident Response: Includes automated responses to threats, minimizing damage and downtime.
Behavioral Analysis: Uses advanced analytics to identify anomalies and suspicious patterns.
Find out how shift-left and shift right security when combined, create a comprehensive cloud security strategy in our part 2 of the blog!