Discover how Cloud Detection and Response (CDR) and Kubernetes Detection and Response (KDR) offer a sophisticated, cloud-native security solution for threat detection, response, and prevention.
Introduction:
As organizations increasingly migrate to the cloud, the complexity of securing these environments has grown exponentially. Traditional security models, like Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR), focus on monitoring and responding to threats at the endpoint level. However, cloud environments demand a more nuanced approach—one that goes beyond simply applying EDR principles to the cloud. This is where Cloud Detection and Response (CDR) and Kubernetes Detection and Response (KDR) come into play, offering a sophisticated, cloud-native solution for threat detection, response, and prevention.

Threat Detection & Response in the Cloud
At its core, Cloud Detection and Response (CDR) revolves around the real-time detection and response to active security threats. The key activities include:
- Threat Monitoring: Continuous monitoring for suspicious activities and potential threats, tailored to the cloud environment’s unique challenges.
- Incident Response: Rapid response to and mitigation of detected threats to minimize impact and prevent lateral movement.
- Threat Hunting: Proactive search for hidden threats within the cloud environment, identifying risks before they escalate.
CDR and KDR are not just cloud-based extensions of EDR. They are purpose-built to handle the intricacies of cloud infrastructure, which includes ephemeral containers, dynamic workloads, and complex microservices architectures. The analogy to EDR/MDR is helpful, but it’s crucial to recognize that CDR/KDR solutions are uniquely designed to address the specific needs and challenges of cloud-native environments.
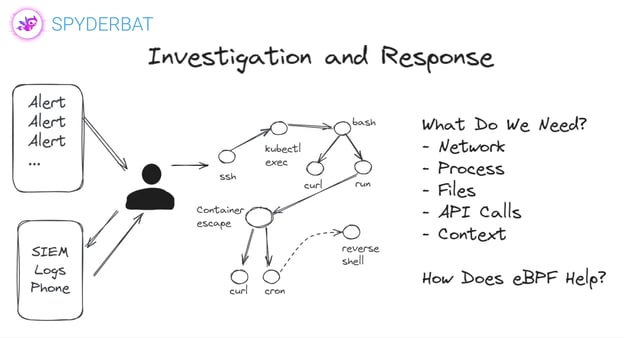
The Crucial Role of Runtime Security in CDR
A critical component of CDR is its integration with runtime security, which is essential for maintaining continuous protection in dynamic cloud environments. Runtime security focuses on monitoring and defending applications while they are executing, which is especially important in cloud environments characterized by constantly changing workloads and ephemeral resources like containers. CDR extends the traditional concepts of runtime security by providing continuous visibility and control over the execution environment. This ensures that threats are detected and mitigated in real-time, even as applications and services scale or change state. By linking runtime security with CDR, organizations can achieve a holistic approach to cloud security that not only detects threats but also protects against them as they occur, preventing potential breaches and minimizing impact.
The Pain Points: Challenges in Cloud Runtime Security
In cloud environments, security challenges are more pronounced due to the inherent complexity and dynamic nature of cloud infrastructure. Key issues include:
- Detection Trade-offs: The balance between false positives and false negatives is delicate and often dictated by the size and capacity of the Security Operations Center (SOC) team.
- Zero-Day Attacks: These pose significant challenges as they exploit previously unknown
- vulnerabilities, often before a patch or mitigation is available.
- Custom Applications: Applications with no published Common Vulnerabilities and Exposures (CVEs) make it difficult to detect and respond to threats.
- Ephemeral Containers: Short-lived containers complicate security monitoring and threat detection, as they may not exist long enough for traditional security measures to be effective.
- General Cloud Complexity: The dynamic and scalable nature of cloud environments introduces additional layers of complexity, making it challenging to maintain comprehensive security coverage.
These challenges are exacerbated by the sheer volume of alerts generated, often leading to alert fatigue and the potential for critical threats to be overlooked.
The Solution: Behavioral Context Web by Spyderbat
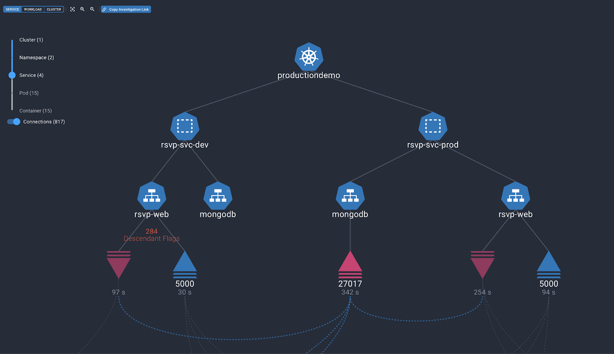
Spyderbat's solution to these challenges is the Behavioral Context Web, a revolutionary approach that records and links all contextual data in real-time. This continuous recording ensures that all processes, connections, containers, pods, clusters, users, and APIs are tracked, maintaining causal links across the entire environment. This extensive recording capability (3 months and more) enables unparalleled visibility into the cloud infrastructure.
How the Behavioral Context Web Changes Everything
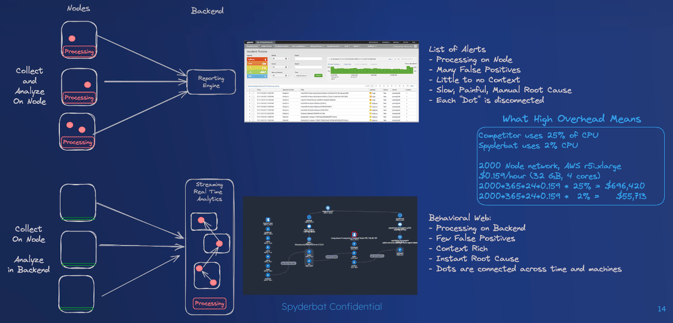
The Behavioral Context Web introduces a paradigm shift in how security alerts are managed and responded to:
- Instant Root Cause Analysis:
- Upon receiving an alert, the specific trace is automatically extracted, encompassing all activity leading up to and following the alert.
- This comprehensive recording eliminates the need to sift through logs, allowing security teams to simply "roll the tape" to understand the full context of the alert.
- The web maps any alert to relevant contextual information, instantly visualizing all necessary details.
- This approach provides root cause analysis and risk impact assessments within seconds, significantly reducing response times and eliminating false positives.
- Alert Reduction by Orders of Magnitude:
- The Behavioral Context Web automatically links related alerts, chaining them into actionable traces.
- These traces are continuously tracked and scored, with alerts raised only when they present a true risk.
- This method provides early detection and automatic triage, reducing the number of alerts by three orders of magnitude and preventing alert fatigue.
- Drift Protection:
- The web continuously monitors for drift from "known good" behavior, instantly detecting deviations that could indicate zero-day attacks or unpatched vulnerabilities.
- New, legitimate behavior from applications can be easily added to a profile, while known good behavior eliminates false positives.
- Profile enforcement can prevent drift, providing robust protection against emerging threats.
Conclusion
Cloud Detection and Response (CDR) represents a significant evolution in how organizations secure their cloud environments. With the complexities of cloud infrastructure, traditional security models are no longer sufficient. Spyderbat's Behavioral Context Web offers a cutting-edge solution that not only addresses these challenges but also enhances security teams' ability to respond to threats quickly and accurately. By reducing false positives, providing instant root cause analysis, and protecting against drift, this approach ensures that organizations can confidently navigate the cloud's ever-evolving threat landscape.
Spyderbat: Cloud Detection and Response built for Kubernetes and Multi-Cloud
Spyderbat provides true cloud detection and response at runtime for Kubernetes and Multi-cloud. See how you can:
- Gain complete visibility and control in all regions by harnessing the power of eBPF Spyderbat eBPF Nano Agents.
- Collect kernel-level workload data with negligible performance impact and no management overhead (using less than 2% of resources).
- Visualize runtime activity, detect attacks, recognize anomalies, and automatically take the right action to protect app behavior and minimize downtime.
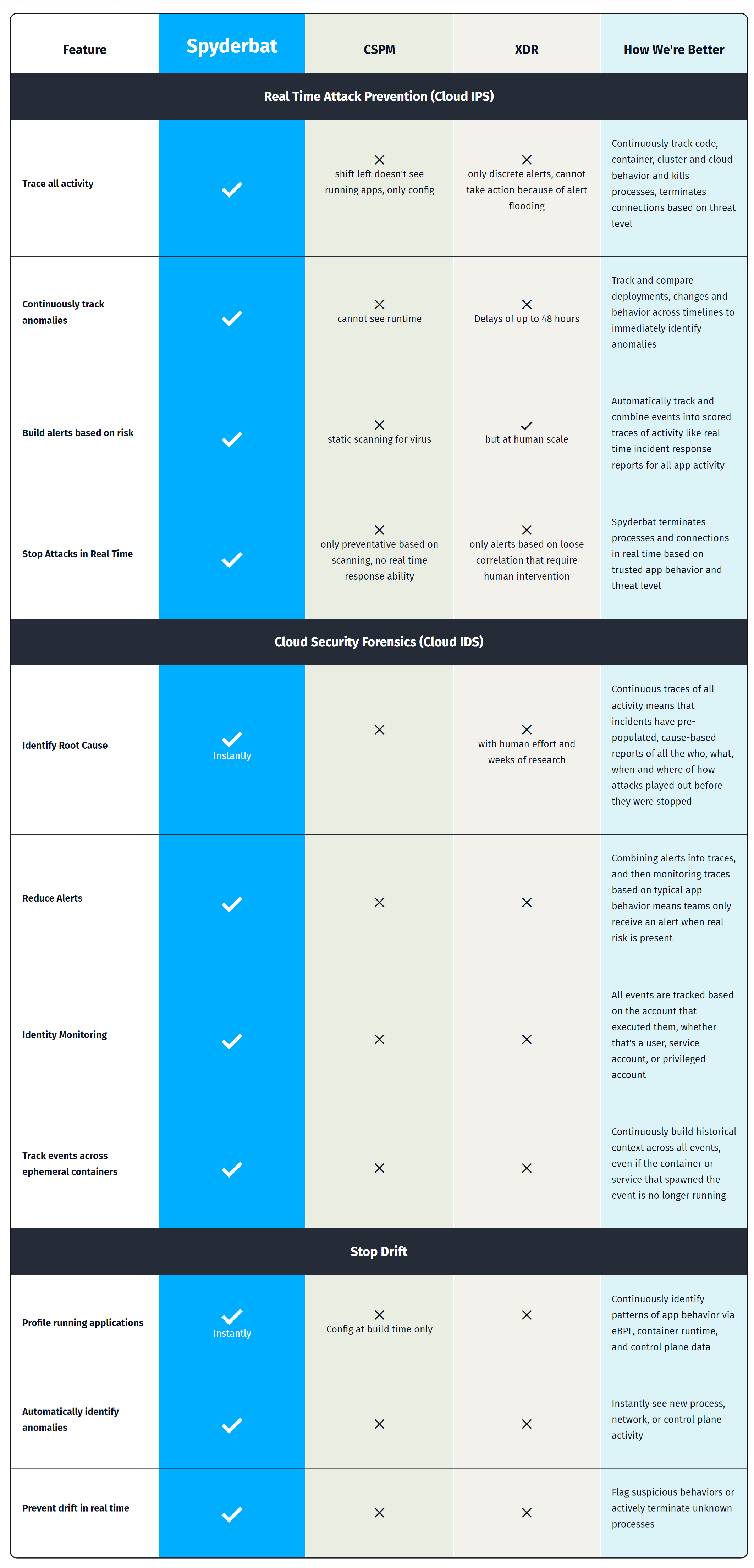
Compare Spyderbat's critical capabilities with other cloud security solutions to see where they fall short. Elevate your cloud runtime security.