Discover What Is at Risk: Real-World Examples of a RCE CUPS Attack, and How to Detect, Investigate, and Respond in Minutes with Spyderbat (Powered by eBPF)
Introduction:
During this week, the security community has discovered a RCE vulnerability in Common UNIX Printing System (CUPS), a widely-used printing protocol in UNIX systems. While the scores for the CVEs involved are not set in stone, the highest among them may be given a higher severity score than Heartbleed.

Impact: Which Systems can be Exploited?
Systems running the cups-browsed Linux service may be exploited. These services are included in many UNIX system including:
- GNU/Linux distributions
- Free BSD OS
- Google Chromium
- Oracle Solaris
- And more...
Misconfigurations and weaknesses in CUPS can be exploited by attackers to gain unauthorized access or control. Key attack vectors include:
- privilege escalation
- print job manipulation
- highlighting the security risks often overlooked in CUPS setups
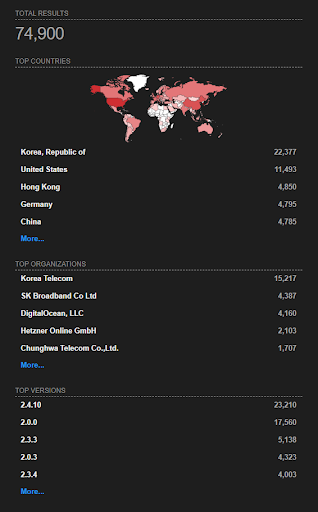
This report above shows the number of devices exposing the port used by CUPS on the open internet. If, configured without proper authentication these systems could be affected immediately.
Real World Example
A real world example of this is if a remote attacker adds or replaces existing printers (printer drivers) with malicious ones. When a print job is executed through the malicious printer driver, it can trigger an execution of malicious code. The malicious code, when executed can
- Take over the privileges of the IP user
- Install remote access trojans to maintain access even after the device has been patched
- Exploit additional vulnerabilities and eventually gain root access to your entire system and infrastructure including on-prem, hybrid, and multi-cloud / Kubernetes.
The Spyderbat threat investigations team ran a real world example of how to detect, investigate and respond to this particular attack.
How to See If You Are Impacted the Traditional way
Check for the services:
- systemctl list-units | grep cups
Disable the services:
- systemctl stop cups-browsed
- systemctl disable cups-browsed
.png?width=1393&height=519&name=image%20(15).png)
These commands must be ran on every system for a full vulnerability scan. Want to find a faster way to check? Trying to find processes executed under foomatic-rip? Try Spyderbat!
How to See If You Are Impacted (Using Spyderbat) in minutes
Using Spyderbat, built on eBPF, you can determine instant root cause with our flashback feature in minutes eliminating the pain of scanning security events and logs.
To discover if you are impacted by the CUPs vulnerability, try Spyderbat’s free tier (forever free) to detect, investigate, and respond (for Linux, Hybrid, and Multi-Cloud, and Kubernetes).
Detection and Investigation
You can detect the existence of the cups-browsed service in 1 of two ways
- Search for processes named cups-browsed using Spyderbat's search system
- Generate a CUPS Assessment Report to get a breakdown of affected machines. These machine must be running the Spyderbat Nano Agent dictated by the size and capacity of the Security Operations Center (SOC) team
.png?width=417&height=425&name=image%20(12).png)
.png?width=372&height=425&name=image%20(11).png)
You can detect exploited systems using Spyderbat Scout detections and:
- Processes executed via this vulnerability show up under formatic-rip.
- Suspicious processes will get flagged and identified as being a descendent of formatic-rip
- We associated the flag with the CVEs listed in the original blog post
- Those flags are searchable and can be added to a dashboard
- Alternatively the user can search for processes that have foomatic-rip as an ancestor
You can also take action via the manual response actions killing the processes associated with cupsd and cups-browsed
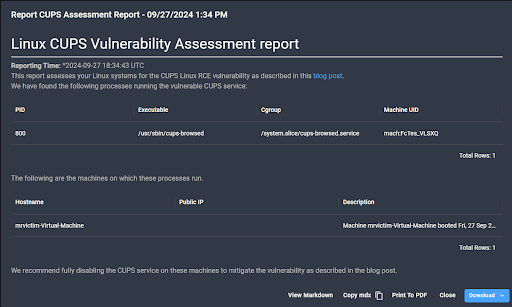
Spyderbat’s Threat Investigation team has created a Linux Cups Vulnerability Assessment Report:
Spyderbat's solution to these challenges is the Behavioral Context Web, a revolutionary approach that records and links all contextual data in real-time. This continuous recording ensures that all processes, connections, containers, pods, clusters, users, and APIs are tracked, maintaining causal links across the entire environment. This extensive recording capability (3 months and more) enables unparalleled visibility into your Linux, Kubernetes and or multi-cloud infrastructure.
How Spyderbat's Behavioral Context Web Changes Everything for Linux, Kubernetes, and Multi-Cloud
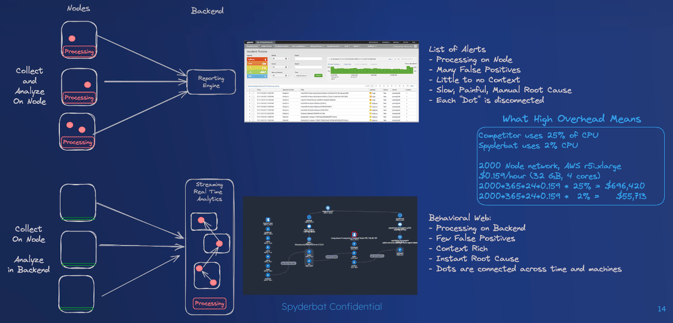
The Behavioral Context Web introduces a paradigm shift in how security alerts are managed and responded to:
- Instant Root Cause Analysis:
- Upon receiving an alert, the specific trace is automatically extracted, encompassing all activity leading up to and following the alert.
- This comprehensive recording eliminates the need to sift through logs, allowing security teams to simply "roll the tape" to understand the full context of the alert.
- The web maps any alert to relevant contextual information, instantly visualizing all necessary details.
- This approach provides root cause analysis and risk impact assessments within seconds, significantly reducing response times and eliminating false positives.
- Alert Reduction by Orders of Magnitude:
- The Behavioral Context Web automatically links related alerts, chaining them into actionable traces.
- These traces are continuously tracked and scored, with alerts raised only when they present a true risk.
- This method provides early detection and automatic triage, reducing the number of alerts by three orders of magnitude and preventing alert fatigue.
- Drift Protection:
- The web continuously monitors for drift from "known good" behavior, instantly detecting deviations that could indicate zero-day attacks or unpatched vulnerabilities.
- New, legitimate behavior from applications can be easily added to a profile, while known good behavior eliminates false positives.
- Profile enforcement can prevent drift, providing robust protection against emerging threats.
Spyderbat: Cloud Detection and Response built for Linux, Kubernetes, and Multi-Cloud
Spyderbat provides true detection and response for Linux, Kubernetes and multi-cloud. See how you can:
- Gain complete visibility and control in all regions by harnessing the power of eBPF Spyderbat eBPF Nano Agents.
- Collect kernel-level workload data with negligible performance impact and no management overhead (using less than 2% of resources).
- Visualize runtime activity, detect attacks, recognize anomalies, and automatically take the right action to protect app behavior and minimize downtime.
Compare Spyderbat's critical capabilities with other security solutions to see where they fall short. Elevate your Linux, Kubernetes, and multi-cloud security.