Introduction:
Kubernetes has become the backbone of modern cloud-native application deployments, offering immense scalability, flexibility, and automation. However, with its wide adoption comes the pressing concern of securing Kubernetes clusters. A robust security strategy must address every layer of the Kubernetes environment to ensure the integrity and availability of applications. The foundation of Kubernetes security lies in the Four Cs of Cloud-Native Security: Cloud, Cluster, Container, and Code. Each layer is critical in building a secure environment and detecting threats across the cloud-native landscape.

The 4 Cs of Kubernetes Security
- Cloud:
The infrastructure where the Kubernetes cluster operates, whether in a private data center, public cloud, or hybrid environment. Misconfigurations in cloud environments, such as open network ports or excessive privileges, can lead to severe vulnerabilities.
Best Practice: Follow the shared responsibility model, implement cloud security controls, and use tools for cloud security posture management (CSPM). Encrypt all data in transit and at rest.
- Cluster:
The heart of Kubernetes, where orchestrating workloads happens. Securing the Kubernetes cluster is essential as it manages container deployments, networking, and storage.
Best Practice: Lock down API access, use Role-Based Access Control (RBAC), and ensure that the etcd datastore is encrypted. Ensure secure communication between the control plane and worker nodes through TLS encryption.
- Container:
Containers package the application code and dependencies. A compromised container can lead to lateral movement within the cluster.
Best Practice: Use minimal base images, regularly update container images, scan images for vulnerabilities, and employ container runtime security to detect and defeat threat activity
- Code:
The source code that runs inside the containers. Vulnerabilities in the application code can be exploited if not addressed early in the development lifecycle.
Best Practice: Adopt DevSecOps practices by integrating security scans in CI/CD pipelines. Use static code analysis, secure coding practices, and tools like Software Composition Analysis (SCA) to check for vulnerable dependencies.
Why Holistic Visibility is Crucial for Kubernetes Security
Kubernetes operates as a complex, dynamic environment with multiple layers that need constant monitoring and management. To secure Kubernetes, it's important to take a holistic approach and have full visibility across the entire stack—cloud, cluster, containers, and code. Here’s why this comprehensive view matters:
- Cloud Detection and Response:
Cloud environments are inherently dynamic and distributed, making detection of threats challenging. Having visibility into cloud infrastructure allows for real-time detection of threats, misconfigurations, and anomalies.
Kubernetes clusters run on cloud infrastructure, meaning that cloud detection and response (CDR) should include the monitoring of both cloud-specific events and Kubernetes-specific threats, such as privilege escalations, exposed dashboards, and insecure network configurations.
- Runtime Security:
Security doesn’t stop at deployment; runtime threats like container breakouts, insider attacks, or vulnerabilities in running containers pose significant risks. Monitoring at runtime helps detect suspicious behavior, such as unusual network traffic or file system access.
Implementing runtime security tools that can observe behaviors within containers, pods, and across clusters ensures that security controls are not just static but adaptable to new threats in real-time.
- Shift-Left Security:
Securing Kubernetes requires a “shift-left” approach where security is embedded from the development stage. Vulnerabilities in code or container images, if left unchecked, could lead to compromise when deployed.
A holistic view ensures security starts from the source code and continues through the build, deployment, and runtime phases, providing comprehensive protection at each layer of the Kubernetes lifecycle.
- Incident Response:
With a complete view of the Kubernetes cluster, teams can implement detection and response mechanisms. Visibility into logs, API requests, container runtime behavior, and network policies allows security teams to detect anomalies quickly and respond to threats before they escalate.
Proper logging and monitoring across the 4 Cs ensure faster and more informed responses to potential breaches or suspicious activity.
- Preventing Supply Chain Attacks:
Supply chain vulnerabilities in Kubernetes environments are a growing concern, with attackers leveraging vulnerabilities in third-party images or infrastructure components.
By having end-to-end visibility, you can monitor and audit every component of the Kubernetes environment, ensuring that vulnerabilities from external sources are identified and mitigated quickly.
Best Practices in Kubernetes Security

Here are some essential Kubernetes security best practices to consider when building and securing your Kubernetes clusters:
- Limit API Access:
Control access to the Kubernetes API using RBAC and only grant the least privilege necessary for each role.
Network Segmentation:
Use network policies to restrict traffic between Kubernetes pods and isolate sensitive workloads.
- Monitor and Audit Logs:
Continuously monitor logs from the Kubernetes API server, kubelet, and other critical components to detect unauthorized access or unusual activities.
Harden Nodes: Secure your worker nodes by using operating systems with a minimal attack surface, applying the latest patches, and restricting access to the kubelet API.
Implement Image Scanning: Continuously scan container images for known vulnerabilities and malware.
- Runtime Threat Detection:
Use tools that monitor container and pod behaviors for signs of compromise, such as unusual system calls or privilege escalation attempts.
Ensure Pod Security: Define and enforce pod security policies to prevent privileged containers or unnecessary access to host resources.
Backup and Disaster Recovery: Regularly backup etcd, your cluster's state, and ensure you have a disaster recovery plan in place.
Spyderbat: Detection and Response at Runtime for Kubernetes Security.
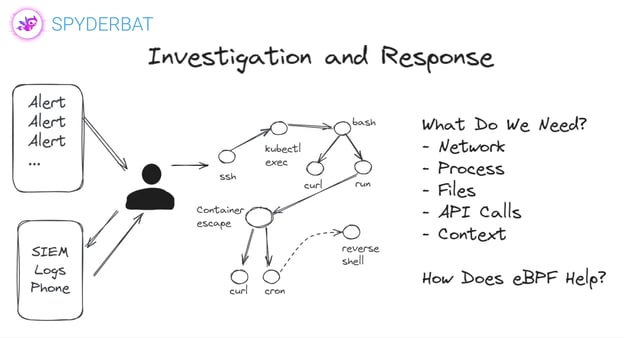
Spyderbat provides a purpose-built SaaS solution for Cloud Detection and Response that targets Kubernetes, Multi-cloud and Linux. Not only is the solution designed to fully leverage cloud and Kubernetes context, but it automates the lions hare of what security teams are challenged with:
- Detect and block attacks
- Reduce the SOC workload by two or more orders of magnitude
- Automatically determine root cause
- Profile Linux services, containers, K8s deployments, services, and clusters to detect and fix defeat attacks, repair misconfigurations, and drift
Behavioral Context Web by Spyderbat
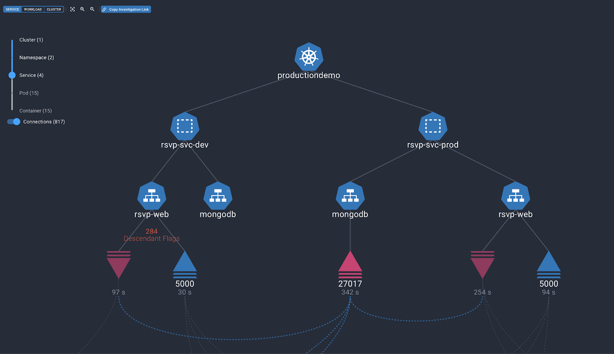
Spyderbat's Behavioral Context Web is a revolutionary approach that records and links all contextual data in real-time. This continuous recording ensures that all processes, connections, containers, pods, clusters, users, and APIs are tracked, maintaining causal links across the entire environment. This extensive recording capability (3 months and more) enables unparalleled visibility into the cloud infrastructure.
How the Behavioral Context Web Changes Everything
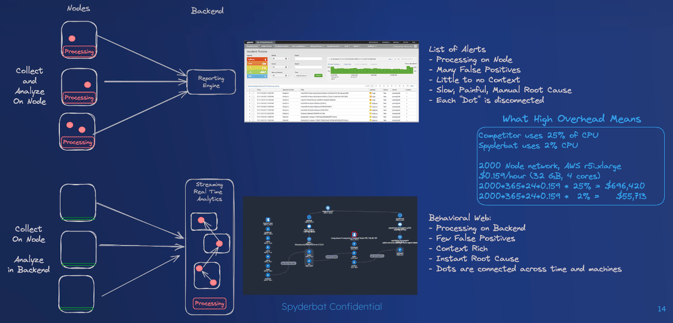
The Behavioral Context Web introduces a paradigm shift in how security alerts are managed and responded to:
- Instant Root Cause Analysis:
- Upon receiving an alert, the specific trace is automatically extracted, encompassing all activity leading up to and following the alert.
- This comprehensive recording eliminates the need to sift through logs, allowing security teams to simply "roll the tape" to understand the full context of the alert.
- The web maps any alert to relevant contextual information, instantly visualizing all necessary details.
- This approach provides root cause analysis and risk impact assessments within seconds, significantly reducing response times and eliminating false positives.
- Alert Reduction by Orders of Magnitude:
- The Behavioral Context Web automatically links related alerts, chaining them into actionable traces.
- These traces are continuously tracked and scored, with alerts raised only when they present a true risk.
- This method provides early detection and automatic triage, reducing the number of alerts by three orders of magnitude and preventing alert fatigue.
- Drift Protection:
- The web continuously monitors for drift from "known good" behavior, instantly detecting deviations that could indicate zero-day attacks or unpatched vulnerabilities.
- New, legitimate behavior from applications can be easily added to a profile, while known good behavior eliminates false positives.
- Profile enforcement can prevent drift, providing robust protection against emerging threats.