Spyderbat was founded by myself, Marc Willebeek-LeMair and Brian Smith. This is our third cyber security startup. Our 25 year journey in cyber began in early 2000 when we founded our first startup, TippingPoint Technologies, which pioneered the intrusion prevention space and, I think, exemplified a bit of our trademark, which is to build really deep tech. Our Intrusion Prevention System was a very complex product of custom hardware and software that sat inline and acted like a network switch, but also had the intelligence to filter out bad traffic. That company was highly successful and was eventually purchased by 3Com. I became the CTO of 3Com and Brian took over my role as CTO of the TippingPoint Division.
Four years later we left 3Com to start another company called Click Security, which was a Big Data Security Analytics company (XDR in today's terminology). Where at TippingPoint we had done everything we could to block bad things using only the context of what was on the wire, Click gathered broader context from multiple sources in order to detect more complex things that couldn’t be detected simply with the data and the context available on the wire. It also provided that broader context to the analyst. Click was purchased by Alert logic and our product became the front end of their security operation center.
It was a fascinating time at Alert logic where they were going through a transition from being an on-prem company to a data center security company to now cloud and so we got a real introduction to all things cloud: clusters, containers, and virtual systems, etc. and I also got a chance to observe their security analysts serving thousands of customers, worldwide, and watching what the daily grind of a security analyst was all about. Which is a highly manual cumbersome grind that companies still follow today and in essence, we concluded that there had to be a better way. This is the reason we founded Spyderbat.

We concluded that the decades old model of generating security alerts and handing them to a human to analyze was broken. To begin with, there are too many alerts so only a fraction are analyzed. Second, the job of analyzing each alert is complex and time consuming so analysts must timebox each investigation. The ignored alerts and limited investigation time is the risk level we accept at a cost we can afford. The fundamental challenge that each analyst faces when investigating an alert is assembling or reassembling the context around that alert at the time it occurred. This manual exercise is extremely laborious, technically intensive and often inconclusive because the data required to rebuild that context is rarely available.

We decided to flip the script and asked what if rather than trying to reassemble this context every time after an alert, we maintain a continuous record of all the context beforehand and use that to automatically curate and define alerts? What I mean by all the context is the very specific causal linkages between a process that launched a process and that a process opened a connection to another process and that process download a file, etc,. and who the user was during that activity, what systems they were on, what systems they laterally moved to. So we’re talking about a broad contextual behavioral view of the entire infrastructure, not just a single node on a single machine for a single instance, but across all time, we’re talking months of time continuously recording what’s going on.
This behavioral context web, once we were able to prove that we could implement it at scale, is the game changer. Using a thin eBPF (Linux construct) agent and a highly scalable stream processing SaaS backend we have a unique differentiated technology. It completely changes the way we investigate. It completely changes the way we detect and it really is, such a fundamental shift in the way cyber security and corporations protect themselves.
We start with this behavioral context web and build on it. Our Flashback function can take any third-party alert and map it to this giant graph and in an instant extract the previous chain of events that led to that event and everything that happened since. In essence giving you the full context necessary to answer the important questions: Is this real? What happened? How do we stop it? How do we prevent this from happening in the future? Those questions are answered automatically. Like the GuardDuty DNS alert one customer was getting tied to an ephemeral container which we could easily “rewind” to and show what happened. Or even more interestingly, imagine an intruder using compromised credentials coming into the system on one node, sitting quietly for a few weeks, then moving laterally, possibly changing credentials, planting a backdoor, maybe exploiting an unknown or unpatched vulnerability and moving deeper until finally uploading some malware that gets detected and generates an alert. Well, we would take that alert and Flashback would instantly provide the entire story that may be months long in the making and illuminate all the necessary remediation steps!

Next, with Scout, we change the way you detect. By simultaneously coloring the graph with Spyderbat security events and any 3rd party events, we maintain collections of events that are causally linked by the underlying behavioral context web. We refer to these chains as traces. We maintain live scores for each trace. Hundreds of thousands if not millions of security events reduce to thousands of live traces which in turn reduce to a handful of meaningful traces that require intervention. Traces are stateful and don't forget about even the lowest severity events that occurred months ago. Scout continuously analyzes all traces looking for signs of intrusion. It automates the hunting process. Intervention can come in the form of an alert or an automated action to kill a process, quarantine a container or any variety of surgical actions. Furthermore, traces help suppress false positives and only a handful see the light of day to be acted upon. So rather than having thousands of alerts every day you only have a few and the time it takes to investigate those alerts goes to minutes rather than hours or days.
Finally, with Guardian, we provide a new, highly resilient, layer of protection. Since the behavioral context web tracks every nuance of your application behavior we can take a snapshot and create an instant profile. With that profile we instantiate guardrails and immediately detect any drift which signals that something is amiss. Those guardrails can be enforced to prevent drift or simply notify and explicitly indicate the detailed nature of the drift. This protection is resilient to any known or unknown vulnerabilities or new attack vectors since it is based on what is “known good.”
Ultimately, the Spyderbat solution is based on our unique behavioral context web. It is the foundation of a new approach to detection and response. Furthermore it presents a powerful opportunity for AI. No one has this unique graph and using it to train AI engines and further automate and democratize the detection and response process is exciting.

Marc Willebeek-LeMair
CEO | Co-Founder
Spyderbat
Spyderbat: Next generation runtime security built for Kubernetes and multi-cloud
Spyderbat is the next generation runtime security providing true IDS/IPS, posture management, and remediation in runtime for Kubernetes and Multi-cloud. See how you can:
- Gain complete visibility and control in all regions by harnessing the power of eBPF Spyderbat eBPF Nano Agents.
- Collect kernel-level workload data with negligible performance impact and no management overhead (using less than 2% of resources).
- Visualize runtime activity, detect attacks, recognize anomalies, and automatically take the right action to protect app behavior and minimize downtime.
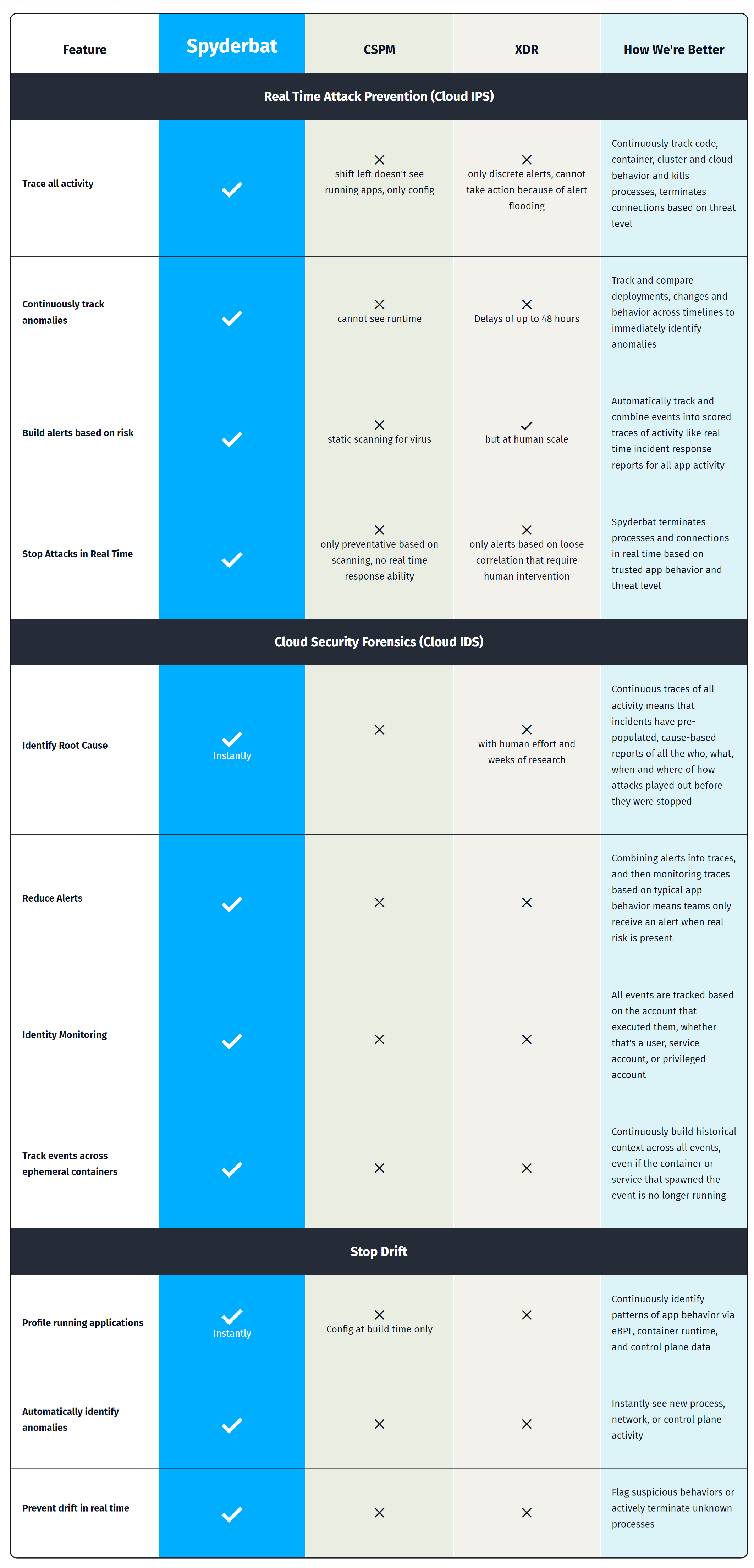
Compare Spyderbat's critical capabilities with other cloud security solutions to see where they fall short. Elevate your cloud runtime security.